The AVENUE concept

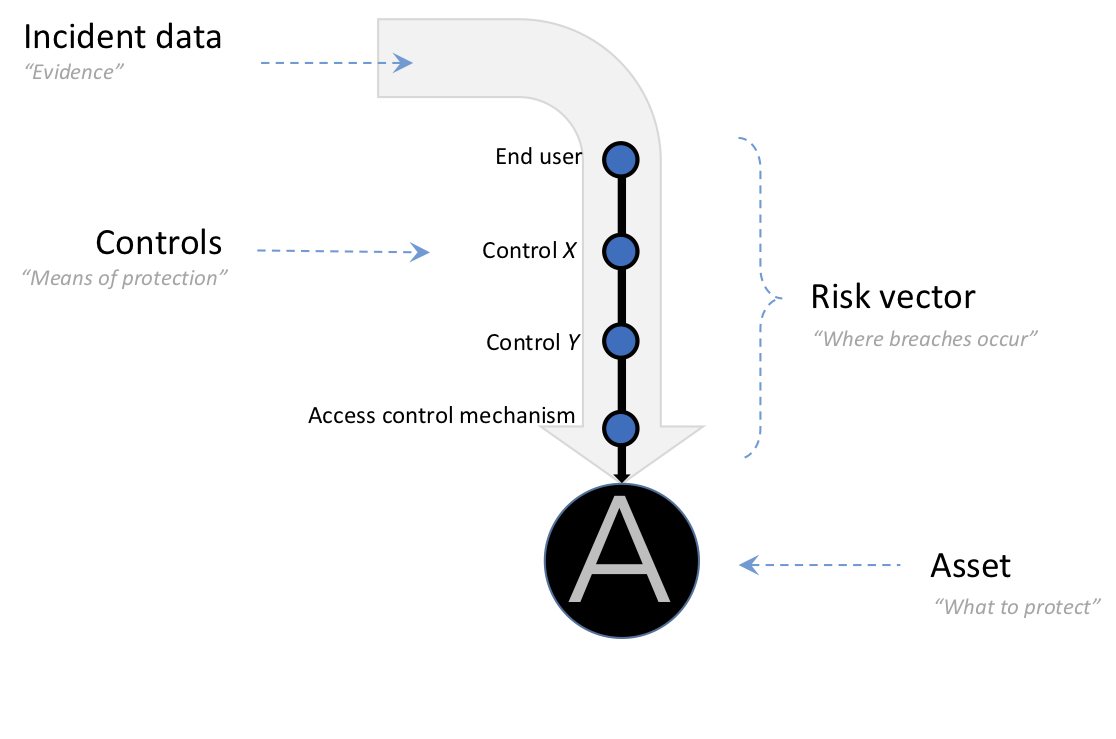
An avenue is traditionally a path with a line of shrubs running along each side, indicating the access to or arrival at an architectural feature, i.e. an asset. In a transferred sense, the concept emphasizes an asset-vector centric view of an organisation. Avenue is also an acronym stemming from “Asset-VEctor with Nodes securing Users and protecting from Enemies”.
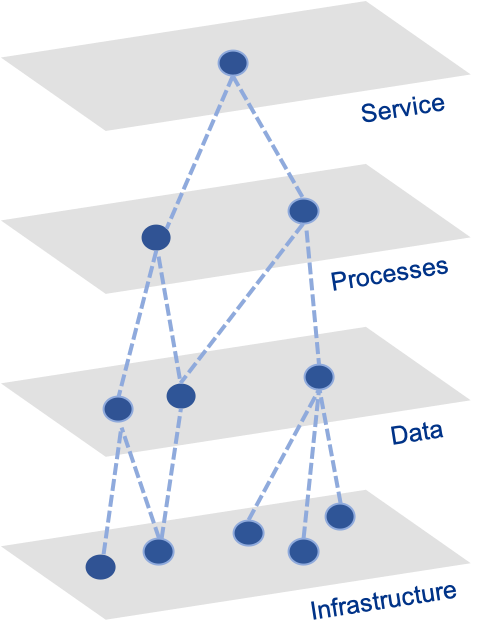
bossanalytics cyberrisk is based on the AVENUE concept compelling the organisation to identify and value the protectable assets, their risk vectors including the security controls in operation to protect them.
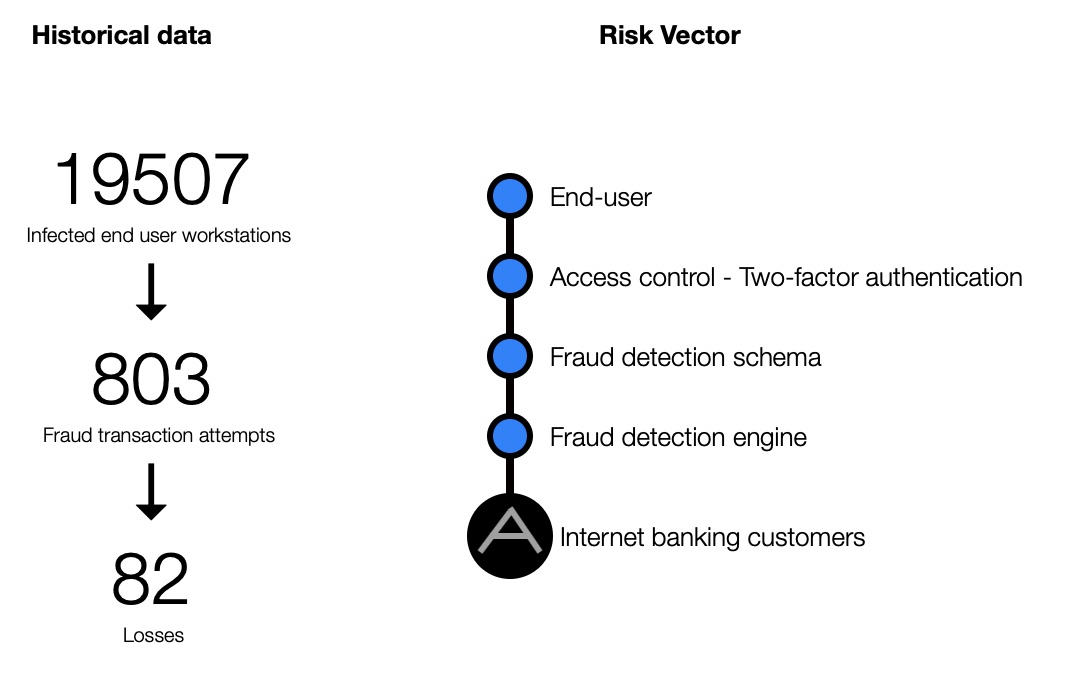
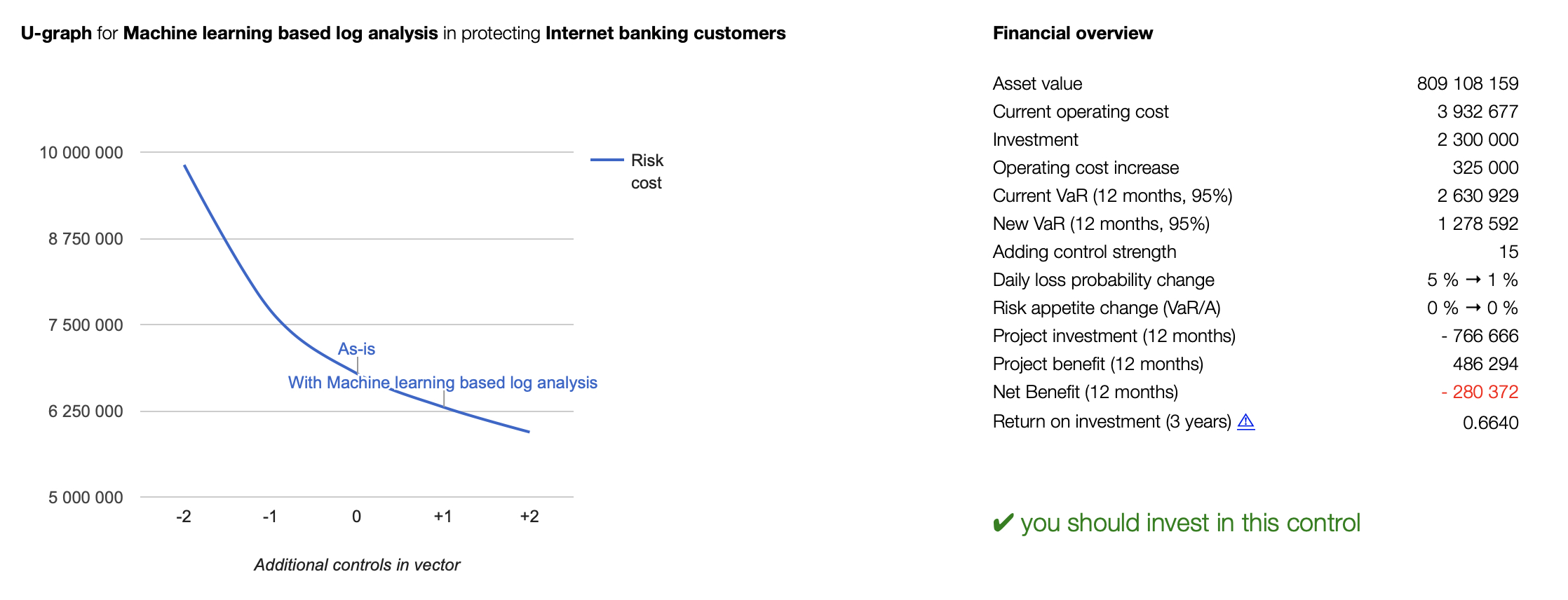
A theoretical loss probability is subsequently calculated per risk vector and asset based on the characteristics of the security controls. When adding actual incident data, the algorithms learn and adapt to make loss predictions more accurately.
This approach forms the basis for connecting your cyber risk endeavour to the business level of your organisation.